Introduction
If the environment includes web applications in private and public locations, do the following to start monitoring:
- Step 1: Whitelisting IP Address
- Step 2: Implementing instrumentation strategy
- Step 3: Onboarding resources and users
- Step 4: Enabling resource management profiles
- Step 5: Setting up synthetic monitors
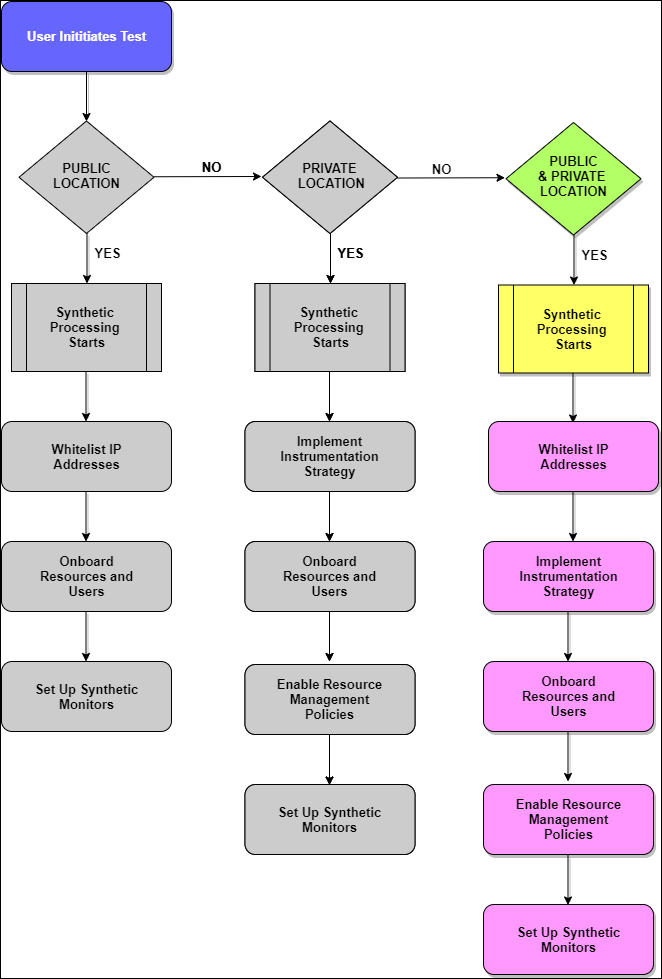
Monitoring from Private and Public Locations
Steps to monitor from private and public locations
Step 1: Whitelisting IP Address
Whitelisting IP Address is an important factor to enable access to the added monitors from each location. Refer to the following table to understand the whitelisted IP addresses of OpsRamp public synthetic servers.
| Location | IP Address |
|---|---|
| Atlanta, US | 52.5.71.217 |
| California, US | 54.215.29.242 |
| Fremont, US | 54.215.29.242 |
| New Jersey, US | 3.20.8.251 |
| Canada Central | 15.223.94.77 |
| London, UK | 35.177.101.67 |
| Frankfurt | 3.127.157.150 |
| Singapore | 52.77.7.64 |
| Japan | 13.113.179.153 |
| Tokyo | 172.105.225.68 |
| Mumbai, India | 3.6.241.204 |
Step 2: Implementing instrumentation strategy
To monitor any synthetic resources, install Gateway (Version 5.0.0 or above).
To understand the supported choices and recommendations to instrument your environment for monitoring, see Instrumentation Choices.
Step 3: Onboarding resources and users
Onboarding is the process of setting up OpsRamp to discover and manage your environment. Before using the platform, the primary requirement is to create an account to do the desired tasks for your organization. For more information, see Account Management.
Step 4: Enabling resource management profiles
Use the Gateway version 5.0.0 or above to enable internet and intranet monitoring of the infrastructure, after enabling Synthetics Agent.
Toggle from OFF to ON to enable Synthetics Agent from Setup > Resources > Management Profiles > View Management Profile.
Step 5: Setting up synthetic monitors
Prerequisites
- Assign a synthetic template to initiate synthetic monitoring using Assign Templates or Device Management Policies.
- Set permissions for Device Create, Device Edit, Device View, and Device Manage to create, edit, view, and delete the configured synthetic monitors respectively.
- Verify if the role assigned to you contains access to all resources. Otherwise, you cannot delete a synthetic monitor.
Configuring synthetic monitors according to the requirement enhances synthetic security and stabilizes IT operations process flow. For more information, see Creating synthetic monitors.