Introduction
OpsRamp provides a rich set of capabilities to help you manage users' access to OpsRamp. Access controls encompass these areas:
- Authentication: How users are authenticated to access OpsRamp.
- Role-based Access Control: What permissions an authenticated user has within OpsRamp.
Authentication
OpsRamp supports the following authentication options.
Native user management and authentication
OpsRamp comes with built-in user management and authentication. You can create user accounts and provide authenticated access using OpsRamp native authentication capability.
Single Sign-On (SSO)
OpsRamp integrates with several SAML compliant SSO providers. OpsRamp user accounts can be authenticated against these SSO providers.
Two-factor authentication
OpsRamp supports multiple two-factor authentication options for more security. Two-factor options include support for:
- Time-based One-Time Password (TOTP)
- FIDO Universal 2nd Factor (U2F) based solutions.
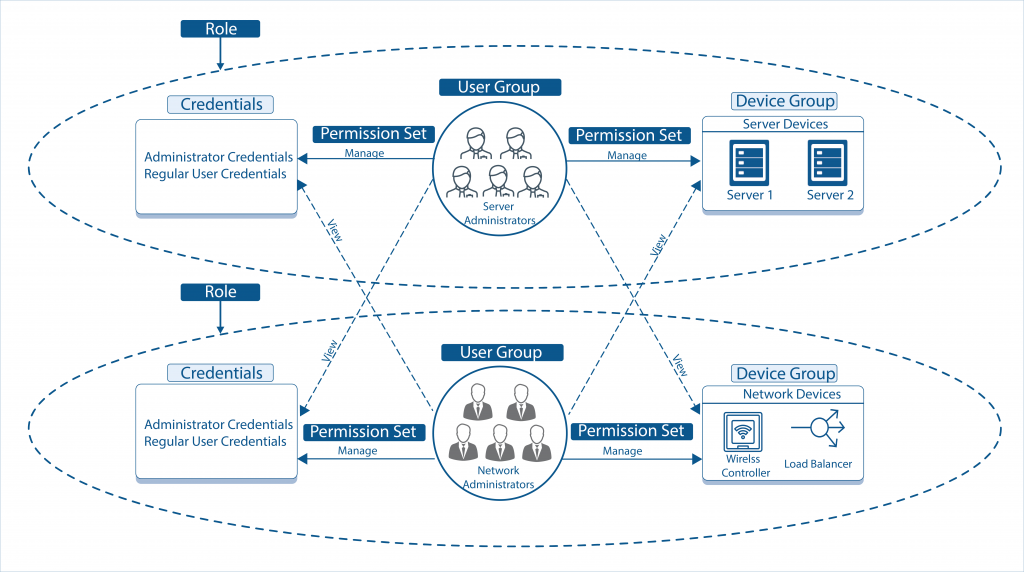
Role-based access control
Using roles, you can control what actions an authenticated user can do within OpsRamp. You can restrict users' access in terms of:
- Resources that a user can manage. For example, a user can only manage network resources.
- Credentials to which a user has access. For example, a user can only view non-admin credentials on servers.
- Actions that a user can take. For example, a user cannot launch a remote consoles.
- Locations (IP addresses) from which a user can access OpsRamp. For example, a user can only access OpsRamp from within the corporate network.