Introduction
Onboarding involves designing management policies for your enterprise operations and for the resources you want to monitor, followed by implementation steps to configure resource discovery and monitoring.
The following figure shows the design and implementation steps.
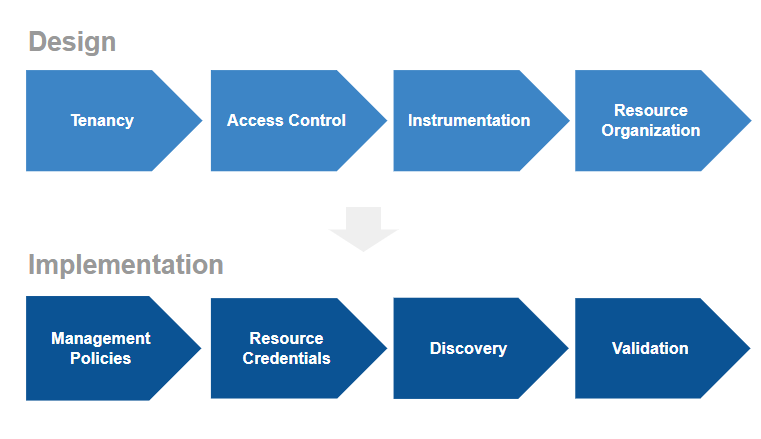
Onboarding Process
The following sections summarize each of the onboarding steps. See the Concepts Guide and Platform documentation for more detailed information.
Design
Tenancy
Tenancy refers to partitioning your environment into client entities. A client can represent:
- a business unit or department.
- locations where resources are deployed, such as public cloud accounts or data centers.
- resources allocation policy, such as development, staging, or production.
It is recommended that you define a tenancy structure that best matches your organizational structure.
Access control
Access control authenticates users and grants permissions to user according to role. Access control design options include:
- single sign-on (SSO) using an external SSO system or native authentication.
- two-Factor authentication.
- providing user accounts at the client level or limiting user accounts at the organization, or partner, level.
- defining roles and access levels for the role.
Instrumentation
Built-in instrumentation is provided to collect metric data. You can specify the type of instrumentation to use depending on the resource type.
Resource organization
Organize your resources into logical categories, including:
- resource groups that logically associate resources.
- sites, which are resources residing in the same geographical location.
- service maps, which logically group resources that provide a service.
Resource organization helps you manage your environment at scale because you can reason about resource classes instead of individual resources.
Implementation
Management policies
Resource management policies simplify onboarding new resources by automating actions performed on the resource when the resource is discovered. Automated actions include assigning or associating:
- monitoring templates
- availability definitions
- knowledge base articles
- credentials
- jobs
- custom attributes
Resource credentials
Access credentials are needed to discover and monitor resources, such as SNMP credentials to manage SNMP-enabled resources. Credentials need to be collected and put in the credential store.
Discovery
Discovery finds and onboards managed resources. Numerous integrations are supported for discovering common resources.
Validation
To validate that resources are successfully onboarded, view the dashboard infrastructure list page, and locate the resource. For a more complete validation, it is recommended that you use the reporting feature, which provides the following information:
- a full inventory of onboarded resources
- the status of onboarded resources
Next steps
See Instrumentation Reference for a list of the options available for discovery and monitoring.
See Getting Started for step-by-step instruction for onboarding servers and installing an agent.